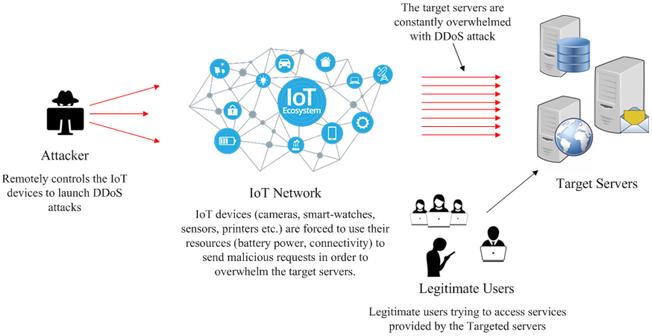
Internet of Things (IoT) devices have been the primary force behind the biggest distributed denial of service (DDoS) botnet attacks for some time. It’s a threat that has never really diminished, as numerous IoT device manufacturers continue to ship products that cannot be properly secured.
A10 Networks, a leading application delivery controller manufacturer, has been keeping tabs on DDoS attacks around the globe for several years now. The company’s quarterly State of DDoS Weapons Report provides a very useful snapshot of the current activity and threat level. The recently-published report for the fourth quarter of 2019 is noteworthy in identifying some new trends that are amplifying DDoS attacks, including a common vulnerability in the WD-Discovery protocol that is being widely exploited and the use of autonomous number systems (ANS) to track attacks back to their source. The report also begins to explore how the rollout of 5G will impact DDoS attacks.
The current state of DDoS attacks
DDoS attacks continue to grow in number and frequency. Behind them are the same botnets that have been plaguing the world for years, composed in no small part of IoT devices that have non-existent or inadequate passwords, inability to patch exploitable firmware, or holes in the authentication and data transfer ecosystem. Automated attacks on known vulnerabilities have granted cyber criminals extensive ability to quickly assemble or grow a botnet.
The report finds that these botnets are most frequently composed of devices located in China, with the United States and the Republic of Korea nearly tied for second place. However, the most active botnets appear to be operating out of Brazil.
Mirai continues to be the malware of choice for botnets. The culprit behind the massive October 2016 attack, Mirai primarily targets IoT devices that run on Linux.
The most rapidly increasing trend this quarter is the use of WS-Discovery (WSD) to amplify DDoS attacks. WSD is one of the most commonly used protocols for discovering and contacting nearby devices. The DDoS attacks make use of WSD hosts, of which there are over 800,000, to amplify the effectiveness of the attack by up to 95%.
The problem with WSD servers is that they are often configured to answer unauthenticated requests. Botnets are perfectly positioned to take advantage of this vulnerability. Small requests that spoof the victim’s IP address can be fed to these servers by each of the compromised devices without raising any alarms.
Why DDoS attacks are getting worse
In addition to continuing to rope in more vulnerable IoT devices, amplification techniques are providing attackers with immensely more “bang for the buck.” These techniques existed prior to the use of WSD. Simple Network Management Protocol (SNMP), Simple Service Delivery Protocol (SSDP) and Trivial Transfer File Protocol (TTFP) have been used in this way for some time and continue to be among the leading amplification methods.
The majority of DDoS attacks are now amplified in this way, particularly the largest of them. This technique was used in the record-breaking attack on GitHub in 2018, along with nearly all of the largest attacks that took place in 2019. Attacks like WSD are particularly potent as they can slip through the cracks of many automated defenses; they make use of a type of port through which this type of traffic is rarely blocked.
DDoS attacks and 5G
The report finds that the introduction of 5G will “dramatically expand” DDoS attacks. Pre-5G, A10 calculates that 127 new IoT devices are being connected per second.
The primary driver of growth will be the addition of a huge number of IoT devices to the global network thanks to the general increase in bandwidth and reduction of latency. In addition to simply adding raw numbers of exploitable devices, lower latency means that effective response time to DDoS attacks will be reduced to seconds rather than minutes.
However, the study points out that these factors will also provide a significant boost to automated security responses based on artificial intelligence and machine learning systems.
Present and future solutions
In terms of preparing for the future of 5G DDoS attacks, A10 is recommending that organizations implement advanced real-time threat intelligence with automatic signature extraction capabilities as soon as possible.
How can organizations protect against these amplified attacks today? The vast majority of these techniques prey upon misconfigured IoT devices. The WSD attack in particular relies on one vulnerable device creating an opening for attackers to make use of any other IoT devices within its range to drive massive amounts of traffic.
Standard current best practice for protecting against amplified IoT DDoS attacks involves having two lines of defense: an initial local system with automated detection and filtering capabilities, and a secondary load balancing cloud system that can activate during a large attack to absorb and redirect excess traffic to preserve user experience.
Attackers are taking advantage of the common configuration on WSD servers that answer unauthenticated requests to run #DDoS attacks. #respectdataClick to TweetUnfortunately, these attacks can never truly be eliminated unless all of the vulnerable servers are taken offline. While these servers will eventually become outmoded and need to be replaced, expect this process to take a very long time.








